Elementor users who haven’t updated recently will want to get on the latest version 3.1.4 as soon as possible. Researchers at Wordfence disclosed a set of stored Cross-Site Scripting (XSS) vulnerabilities in the plugin to its authors in February, which was partially patched at that time and additional fixes were released the second week of March.
Wordfence summarized the vulnerabilities in a post published yesterday, accompanied by a detailed walkthrough of how an attacker might compromise sites using Elementor:
These vulnerabilities allowed any user able to access the Elementor editor, including contributors, to add JavaScript to posts. This JavaScript would be executed if the post was viewed, edited, or previewed by any other site user, and could be used to take over a site if the victim was an administrator.
Many of the plugin’s “elements,” or components, accept an html_tag parameter, which was output without escaping and could be set to execute a script. A few of the vulnerable elements include the column, accordion, heading, divider, icon box, and image box.
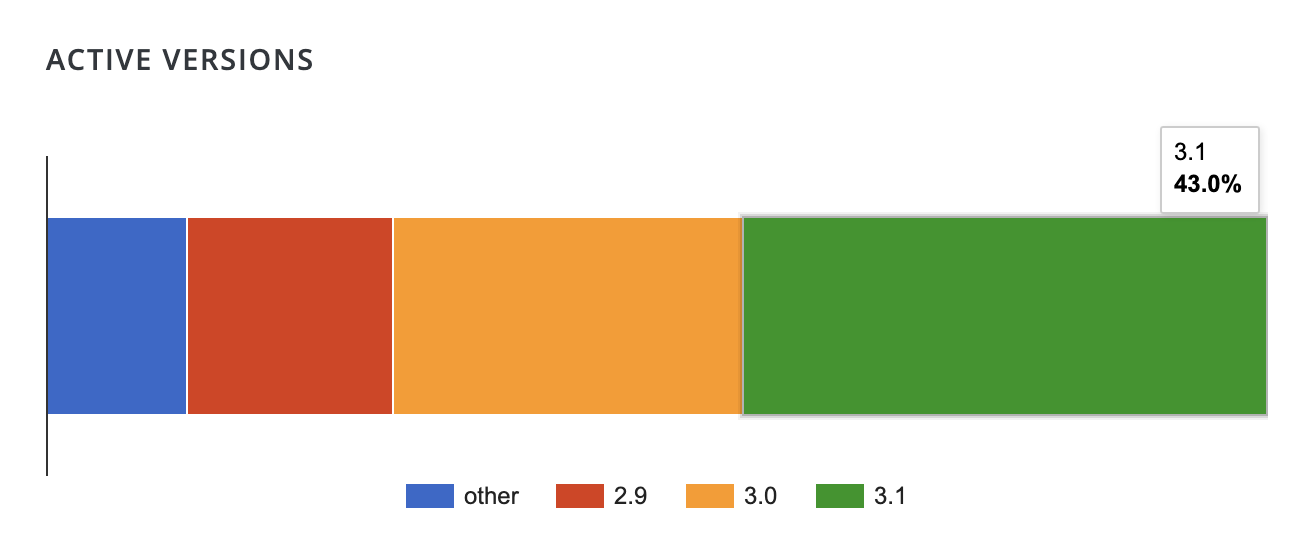
At the time of publishing, less than half of all Elementor installs are running on version 3.1.x, leaving millions of sites still vulnerable. Wordfence confirmed this morning that they are not currently seeing active exploits against these vulnerabilities.
“Due to the privileges required, we expect it to be used primarily in targeted attacks rather than widespread attempts,” Wordfence security researcher Ram Gall said. “That is, it is likely to be used for privilege escalation once an attacker has been able to get a foot in the door, rather than a complete start-to-finish exploit chain. This is going to be more of a concern for sites that have many contributor or author users, as this means a wider attack surface. The main reason this is a concern is the sheer number of installations.”
Gall, who discovered the vulnerabilities, described a scenario in which they are most easily exploited. A contributor on the site re-uses a password that has been in a data breach. The attacker finds that password, logs in, and adds a post with malicious code. The administrator sees the post from the contributor in the admin. Visiting that post will run the malicious JavaScript in the browser, which Gall said could infect the site with new rogue admin accounts or code to take over the site.
Apart from a brief mention in the changelog, Elementor did not alert its users to the security issues on the product’s blog or social media accounts:
- Fix: Hardened allowed options in the editor to enforce better security policies
- Fix: Removed
htmloption in Lightbox module to prevent security issues
“Elementor was very responsive initially, though they didn’t keep us updated about the patches after the initial report,” Wordfence representative Kathy Zant said. “They do have a security contact listed on their site, which is always helpful. Often, security researchers have a difficult time identifying and contacting the right person with whom to share vulnerability proof-of-concepts, so we’re always grateful when we’re able to easily start those discussions.”
The latest version 3.1.4 contains the patches for these vulnerabilities, along with fixes for other less severe bugs in the plugin. Elementor users are advised to update as soon as possible to avoid the vulnerabilities being used for site takeover.