It’s common knowledge that WordPress themes and plugins can make your site more vulnerable to attack. However, third-party libraries can also leave your site susceptible to hackers.
Fortunately, there are steps you can take to protect your WordPress installation – even when the security loophole originates from third-party code. This has never been more important, as a critical vulnerability was recently discovered in the library that WordPress uses to send emails.
In this post, we’ll discuss what this new object injection vulnerability is, and why it could spell disaster for your website. We’ll then share three simple ways to protect your site against the PHPMailer vulnerability, plus other site injection attacks. Let’s get started!
An Introduction to Site Injection Attacks
The WordPress core team has a good reputation for addressing vulnerabilities on its platform. However, this popular Content Management System (CMS) doesn’t exist in a vacuum. It’s widely acknowledged that some WordPress themes and plugins can make your site more susceptible to attack. However, third-party libraries may also be putting your site at risk.
Recently, an object injection vulnerability was discovered in WordPress versions 3.7 right through to 5.7.1, due to the PHPMailer library. This open source library is how WordPress manages to send emails without requiring you to perform additional configuration.
An object injection vulnerability occurs when you fail to sanitize user-supplied input correctly before passing it to the unserialize() PHP function. Since PHP permits object serialization, attackers can potentially pass ad-hoc serialized strings to an unserialize() call. This may result in arbitrary PHP object(s) being injected into your application’s scope.
It’s worth noting that WordPress doesn’t allow direct access to PHPMailer. All of these interactions are performed via the WordPress Application Programming Interface (API), which has various built-in defense mechanisms.
For a hacker to exploit the PHPMailer library, your site would need to already have at least one additional vulnerability. In reality, this makes the security loophole difficult to exploit. However, if a hacker already has access to your site, they could use this vulnerability to escalate their privileges and inflict more damage.
A hacker could also use this weak spot to launch several serious attacks. This includes code and SQL injection, application denial of service, and path traversal.
If any of these attacks succeed, then the malicious third-party might deface your site, delete your account, or steal private visitor information. With so much at stake, it’s important to take steps to close every known security loophole, including ones that are difficult to exploit.
How to Protect WordPress Against Site Injection Attacks (3 Ways)
According to security specialists Patchstack, this PHPMailer weak spot is near the highest level of criticality. On a scale of one to ten, using the Common Vulnerability Scoring System (CVSS), Patchstack has assigned PHPMailer a score of 9.8. That’s a concerning rating for any website owner, so let’s see how you can protect your WordPress installation.
1. Keep WordPress Core Up-to-Date
When it comes to protecting your WordPress website, the number one piece of advice is always the same: keep your site up-to-date. After discovering this object injection vulnerability, the WordPress team quickly issued an update that addresses this security issue. If you’re not already running version 5.7.2 or higher, then it’s vital that you update now:
Whenever a vulnerability is discovered, the WordPress team tries to release a security update as soon a possible. However, even regular releases may introduce new security features and defense mechanisms that can help keep this CMS safe.
By default, WordPress auto-updates itself for minor releases. However, to ensure that your site is safe, you may want to consider enabling auto-updates for major releases.
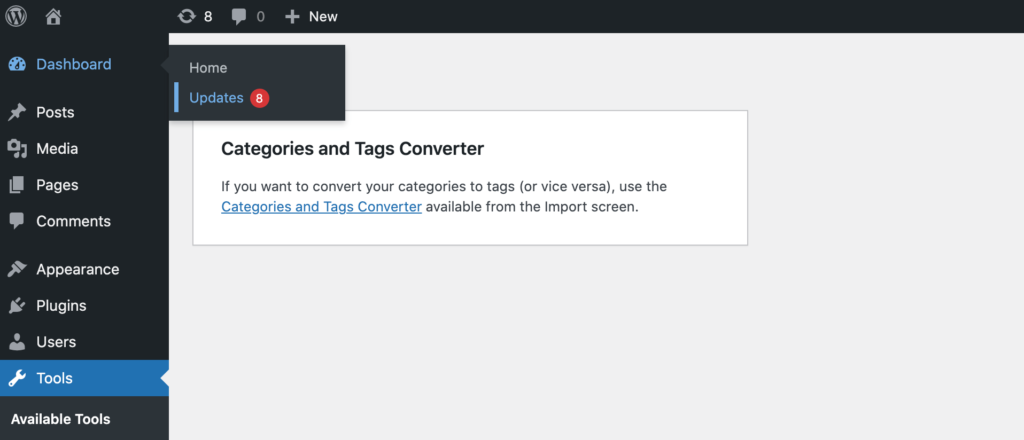
WordPress 5.6 introduced a new auto-update User Interface (UI) that makes it much easier to manage your updates. Assuming that you’re running WordPress version 5.6 or higher, you can activate auto-updates for major releases by navigating to Dashboard > Updates:
Then click on the following link: Enable automatic updates for all new versions of WordPress. From this point onwards, you can be confident that you’re running the latest version of WordPress, which in theory should be the most secure one.
2. Use a Web Application Firewall
To launch an object injection attack in PHPMailer versions 6.1.8-6.4.0, the hacker would need to target Phar Deserialization via AddAttachment with a UNC pathname. This is the path to a folder or file on a network that contains the server name. The good news is that Wordfence’s firewall offers built-in PHAR Deserialization as part of its free and premium plugins:
After activating Wordfence, we recommend placing it in Learning Mode. This mode is designed to help you avoid false positives, which occur when Wordfence wrongly flags legitimate activities as suspicious.
During Learning Mode, continue to interact with your site as normal. This gives Wordfence an opportunity to learn your regular patterns and behaviors. It can then permit all of these actions, while protecting your site against illegitimate actions. To place Wordfence into Learning Mode, navigate to Wordfence > Firewall:
Then, open the Web Application Firewall Status dropdown and select Learning Mode. Wordfence is now monitoring every move you make across your website.
For the best results, we recommend leaving Wordfence in this mode for at least a week. Once you’re confident that Wordfence has collected enough data, activate your firewall by navigating to Wordfence > Firewall. Then, open the dropdown menu and select Enabled and Protecting.
3. Sanitize Your Data
As part of this PHPMailer exploit, a hacker would use the unserialize() function, which takes a string representing a serialized value and converts it to a PHP value. In an object injection attack, a malicious third party might run data through this unserialize() function and choose the properties of those objects. For example, the attacker could construct a payload that enables them to read your files, including the contents of your site’s password directory.
Instead of passing user-generated content directly to the unserialize() function, it’s important to validate and sanitize that data. This can help ensure that any data you do accept is clean, correct, and free from malicious code.
You can sanitize your data using the sanitize_*() series of helper functions. The WordPress Codex provides a simple example demonstrating how you might sanitize user input. It gives the example of a form that expects a string:
In this scenario, you can sanitize this data using the sanitize_text_field() function:
$title = sanitize_text_field( $_POST['title'] ); update_post_meta( $post->ID, 'title', $title );Here, we’re checking for invalid UTF-8, which is variable-width character encoding. This function then removes tags, line breaks, tabs, and extra white space. It also strips out octets, which are units of digital information that consist of eight bits.
In this way, the sanitize function can help you remove any invalid or potentially harmful content before it has a chance to reach your database. This includes any code that a hacker might use to exploit the PHPMailer vulnerability.
Conclusion
While experts agree that the PHPMailer vulnerability is a difficult weak point to exploit, a new critical security threat is always a cause for concern. There’s also a risk that a hacker may use this vulnerability to escalate an attack that’s already in progress, potentially wreaking havoc across your site.
Let’s quickly recap three steps you can take in order to close this security loophole:
- Keep WordPress core up-to-date.
- Use a web application firewall such as Wordfence.
- Sanitize your data using WordPress’ series of helper functions.
Do you have any questions about how to defend against site injection attacks? Ask us in the comments section below!