Since it powers over 40 percent of the web, WordPress is a popular target for attacks. If a hacker manages to break into one WordPress website, they potentially have the key to millions of others – including yours.
Part of keeping your site safe is understanding the risks. As a website owner, this may seem like a daunting subject. However, once you know what you’re up against, you can take the necessary steps to defend your site.
In this article, we’ll discuss the importance of securing your WordPress site, and explore four of the biggest threats against it. Along the way, we’ll share plugins, best practices, and techniques that can help protect your site from each specific danger. Let’s get started!
The Importance of Securing Your WordPress Website
Cyberattacks are on the rise, with fraud prevention specialists Arkose Labs reporting a 20 percent rise in digital attacks in 2020. During this period, Arkose Labs also recorded the highest-ever level of bot attacks, with 1.3 billion detected in total.
Hackers are always coming up with new strategies. There is even evidence to suggest that cybercriminals are trying to use the pandemic to their advantage. The FBI reported a 300 percent increase in cyber crimes since the COVID-19 outbreak began.
WordPress is maintained by a team of highly-experienced developers who work hard to ensure that the platform is secure. However, it’s pretty common for website owners to use a range of WordPress plugins and third-party themes. This adds extra code to your site, which means more potential loopholes that a hacker could exploit.
If a cybercriminal manages to access your site, they can wreak havoc. They might deface it with inappropriate content, remove important data, or defraud your customers. If you haven’t created a backup, you might discover that a hacker deleted your entire site, leaving you with no hope of retrieving your content.
This malicious activity could result in a loss of customer trust, conversions, and revenue. There’s also a chance your site will get blacklisted by the search engines.
If that happens, your content will disappear from the Search Engine Results Pages (SERPs) and your organic traffic will likely plummet. Even if you manage to recover your site, repairing your search engine status may be difficult.
4 Common WordPress Attacks (And How to Avoid Them)
To help keep your site and visitors safe from hackers, it’s vital that you protect against common WordPress attacks. Let’s take a look at four of the most popular threats.
1. Brute-Force Attacks
A brute-force attack is when a hacker attempts to force their way into your dashboard using hundreds or even thousands of known password and username combinations. Brute-force attacks are a popular method of intrusion across all platforms. However, they can be particularly problematic for WordPress.
By default, all WordPress administrators have the same username (“admin”). If you don’t change this automatically-generated username, brute-force hackers already know half of your login credentials – they only need to guess your password.
To help protect your site against brute-force attacks, it’s important to use a unique admin name and follow password best practices. This includes using a minimum of eight characters, plus a mix of upper and lowercase letters, numbers, and symbols.
It’s also smart to avoid common phrases, particularly ones that are frequently associated with passwords, such as “letmein” or “password”. We also suggest steering clear of any words that relate to your website, company, location, or personal details.
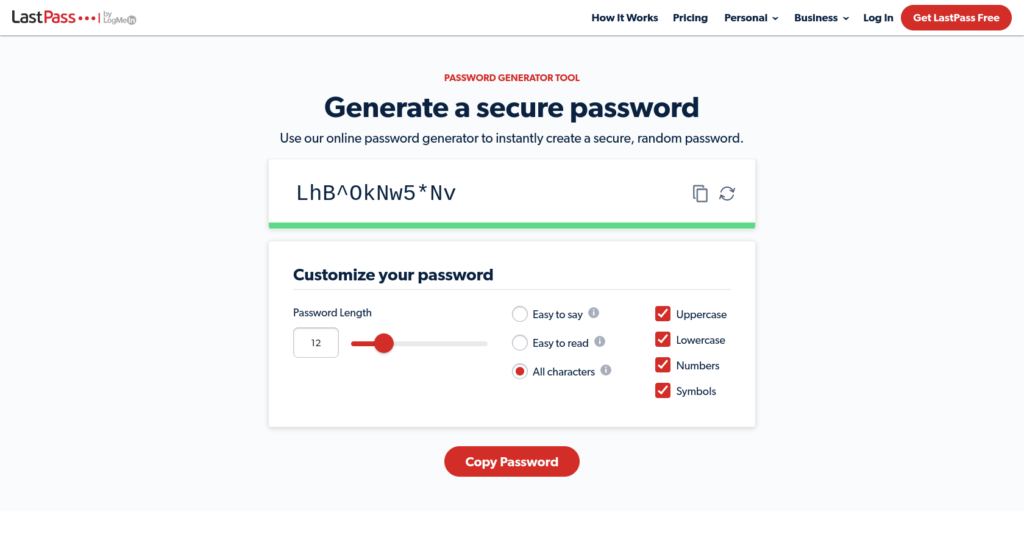
To strengthen your password, it may help to use a generator. Strong Random Password Generator and LastPass are two popular options:
Alternatively, you can create a password from the WordPress dashboard. In your admin area, simply navigate to Users > All Users and select your profile.
Then, under Account Management, you can click on Set New Password to generate a password at random:
It’s also a good idea to limit the number of login attempts on your site, using a plugin such as Limit Login Attempts Reloaded. This can prevent bots from attacking your login page with thousands of passwords in rapid succession.
2. SQL Injection WordPress Attacks
SQL Injection attacks are when an individual attempts to access your WordPress dashboard by injecting malicious SQL queries. Your website’s MySQL database will then run this code, and the hacker may gain entry into your website.
Cybercriminals can launch SQL injection attacks via any section of your site that gathers user input. This means that something as innocuous as a contact form, comments section, or search box could put your database at risk.
Ideally, every input field across your site will be configured to securely validate and sanitize all user inputs before forwarding them to your database. This process ensures that your site only accepts valid data. However, if these input fields aren’t configured correctly, hackers may use them to inject malicious code.
MySQL is vulnerable to injection attacks, so it’s important to keep your database software updated. You should also treat your MySQL login credentials with the same care as your WordPress password.
Using a unique database name can make it more difficult for hackers to identify your database. If you’re using cPanel, you can change your WordPress database name using the phpMyAdmin tool.
Many injection attacks also target themes and plugins that enable visitor input. This is another reason to carefully review all themes and plugins before adding them to your site, and to regularly update third-party software.
3. Cross-Site Scripting (XSS)
A Cross-Site Scripting (XSS) attack is when a hacker uploads malicious JavaScript code to your WordPress website. XSS attacks are typically designed to collect data from your customers, which can be particularly disastrous if your site handles sensitive information such as payment details.
A successful XSS attack may also redirect your visitors to another website of the hacker’s choosing, causing your web traffic to plummet. It can even affect your reputation, especially if the attack routes your customers to a malicious or spammy website.
You can protect your site against XSS attacks by using a Web Application Firewall (WAF) such as the Wordfence plugin. This application-level firewall filters out malicious requests before they have a chance to reach your website:
After activating Wordfence, you can configure your firewall by navigating to Wordfence > Firewall.
4. Distributed Denial-of-Service (DDoS) WordPress Attacks
Distributed Denial-of-Service (DDoS) attacks are often in the headlines, as many high-profile organizations have fallen victim to them. This includes heavyweights such as Netflix and Amazon.
A DDoS attack occurs when hackers bombard a server with requests. Eventually, the server becomes overwhelmed and may even crash. A WAF can identify suspicious requests and prevent them from accessing your website.
The Representational State Transfer (REST) Application Program Interface (API) gives developers the flexibility to use WordPress with other technologies. However, malicious third parties can use the REST API as part of their DDoS attacks. If your website isn’t actively using the REST API, you may want to disable it using a plugin such as Disable WP Rest API.
Similarly, while XML-RPC is useful for enabling pingbacks and trackbacks, hackers could potentially use it as part of their DDoS attacks. If you’re not using XML-RPC, you can disable it using a plugin like Disable XML-RPC-API:
Your hosting provider can also help safeguard your site against DDoS attacks. Some managed WordPress hosting providers such as WP Engine even provide DDoS mitigation tools as standard.
Conclusion
WordPress is one of the most popular Content Management Systems (CMSs) in the world. Unfortunately, this popularity makes your WordPress website a prime target for all types of cyberattacks.
In this article, we discussed four of the most common types of WordPress attacks, and the ways to keep your site safe again them. This includes:
- Brute-force attacks. This is when a hacker uses sophisticated techniques to guess your login credentials. You can protect your site against them by following password best practices and using a password generator such as LastPass.
- SQL Injection attacks. A hacker may inject malicious SQL queries via any user input field. You can make your database more difficult to access by changing its default name.
- Cross-Site Scripting (XSS). Cybercriminals may upload malicious JavaScript code to your WordPress website. Here, it may help to use a WAF, such as the Wordfence plugin.
- Distributed Denial-of-Service (DDoS) attacks. Malicious third parties may attempt to overwhelm your server with requests. You can prevent these attacks by disabling unnecessary APIs and opting for a secure managed WordPress hosting provider such as WP Engine.
Do you have questions about any of the WordPress attacks we’ve mentioned? Let’s talk about them in the comments section below!